Contes:
|
It's a jungle out
there - instead of lions and tigers and bears there
is spam and ransomware and malware. All you want to do is to go online
to communicate with your family and friends, get the news and other
information, maybe look at some videos or listen to some music. And it
feels like you risk being mugged - or at least getting your computer
hijacked by someone who wants you to send them money to set it free.
And senior citizens are especially being targetted - partly because
they often don't have the information or the
experience
online to know how to protect themselves.
You'd like to do the right thing, but advice can be contradictory or
difficult to follow. No wonder an October 2016 article from computer
security company Sophos headlined: ‘Security
fatigue’
leading computer users to more or less just give up.
Don't
give up!
There
are a few things you can do to make your computer more secure and your
online experiences safer without driving yourself crazy - but just as
you've probably learned what makes a street look a bit sketchy and how
to keep yourself personally secure you have to learn to look out for
warning signs that an email, website, file attachment, or download is a
bit sketchy and what to do if you can't avoid it.
|
Note that this workshop is aimed at Windows users - as the
most widely
used desktop and laptop computer platform, Microsoft Windows and its
users are the most targetted. Users of Apple Macintosh computers and
iPhone/iPad (iOS) and Android mobile devices also should think about
digital security, and while some of the suggestions made here will also
apply to them, they should look elsewhere for specific advice:
Mac
malware: Coming soon to a computer near you and
The
Ultimate Mac Security Guide: 20 Ways to Protect Yourself
As well note that there is always a balance between security and
convenience. Having multiple locks on your front door may make your
home more secure but it will take longer to open the door every time
you come home - and someone with a fire axe can still bust your door
in. You'll never be 100% secure online - the trick is to find a balance
between security and convenience that keeps you pretty safe while still
letting you do what you want to do.
Some
general
suggestions:
- If something seems too good to be true, it's usually a
scam. An
email message offering you a share of a large amount of money is
probably wanting access to your bank account. Often scammers try to
take advantage of people's greed.
- Microsoft/Windows/etc will never phone you to tell you that
your
computer is infected. They don't do that!
 Your
bank or online services such as Paypal, Apple iTunes Store,
or others will never email you to tell you your account has been put on
hold or to change your password. They don't do that - if you're unsure
about an email message, go to the company's website - without clicking
a link in the email - and contact them directly. Or phone your bank.
Canada Revenue Agency or the US IRS will never email you to say you get
(or owe) money. Never!
Your
bank or online services such as Paypal, Apple iTunes Store,
or others will never email you to tell you your account has been put on
hold or to change your password. They don't do that - if you're unsure
about an email message, go to the company's website - without clicking
a link in the email - and contact them directly. Or phone your bank.
Canada Revenue Agency or the US IRS will never email you to say you get
(or owe) money. Never!
- If you advertise something for sale on Craigslist, eBay, or
elsewhere and someone contacts you offering you more than your asking
price if you'll ship it somewhere - it's a scam! (see Craigslist's Avoiding Scams
page)
- If you get a vaguely worded email from a stranger or even a
friend suggesting you click on a link (or open an attached file) to see
a funny video or something you'll enjoy, check first (by querying your
friend in a new email - without replying to the first one) before
clicking on the link or opening the attachment.
- Keep a list of your passwords and PIN numbers. (More on
passwords
later).
- We tend to think of hackers as bright pimply-faced teens
and
young adults with a grudge against society. Instead, increasingly
malware is shady big-business making money in fradulent ways from
individual computer users - and increasingly organizations like
hospitals and schools.
Notice that many of these scams and frauds don't involve infecting your
computer with anything - they consist of convincing you to voluntarily
give away bank account or other log-in information. Those that do
involve infecting your computer often work by tempting you or scaring
you into clicking on a link or installing bogus software. This is
called 'social engineering' - it's not really using technology, it's
using psychology to trick
you
into giving them information or infecting your computer. If I phone you
and ask for your password, hopefully you won't just give it to me. If I
phone you and claim to be from your Internet service provider, you're
more likely to give out your password.
- computer virus
- A
computer virus is a program or piece of code that is loaded onto your
computer without your knowledge and runs against your wishes. Computer
viruses can replicate themselves and spread to other computers.
'Classic' computer viruses are rare these days, replaced by other
malware
- phishing - An email
that falsely claims to be a legitimate enterprise in an attempt to scam
the user into surrendering private information to be used for identity
theft. More info: https://www.passwordmanager.com/what-is-phishing/
- spam
- Spam is
electronic junk mail or junk newsgroup postings. Some people define
spam even more generally as any unsolicited email.
- malware -
Unwanted
malicious software - a generic term that includes computer viruses,
spyware, adware (in some cases), ransomware and more
- spyware
- Software
that covertly gathers user information through the user's Internet
connection without his or her knowledge, usually for advertising
purposes.
- adware -
Software
that contains advertisements embedded in the application. Adware is
considered a legitimate alternative offered to consumers who do not
wish to pay for software.
- ransomware
-
Ransomware is a form of malware in which rogue software code
effectively holds a user's computer hostage - often by encrypting user
data files - until a "ransom" fee is
paid.
- firewall -
Firewall is a system designed to prevent
unauthorized access to or from a network. Firewalls are hardware,
software or a combination.
Your first line of defense - see
through fraudulent links and addresses
The
first problem is that often online - both on a web page and in an
email message - you can't easily tell where clicking on a link will
take you. Just because something on a webpage or in an email message
says it goes to (say)
TD
Bank doesn't mean it really
goes to that bank. Even if the text looks like it's a web address:
www.tdbank.com
it could actually point somewhere else - in both cases,
these
links go to my website: http://zisman.ca.
You can see where a link is pointing by letting your mouse
hover
on the
link without clicking. Most current web browsers -
the program you are using to access web pages - has that option
enabled. Try it - point to the underlined boldface words in the
preceeding paragraph. Do you see a web address (URL) - perhaps in small
print in the lower-left corner of your web browser? (If you are using
an older version of the web browser, you may need to enable the 'status
bar' if you're not seeing seeing the real address hiding behind a link).
When you hover your mouse pointer over a link examine the web address
that now appears in the bottom-left of your web browser. If you are
hovering over a link that claims it will take you to the TD Bank and
instead it takes you to http://zisman.ca you should be suspicious. Even
if it looks like the place you want to go is embedded in the middle of
a long link, you should be suspicious. For instance, further down the
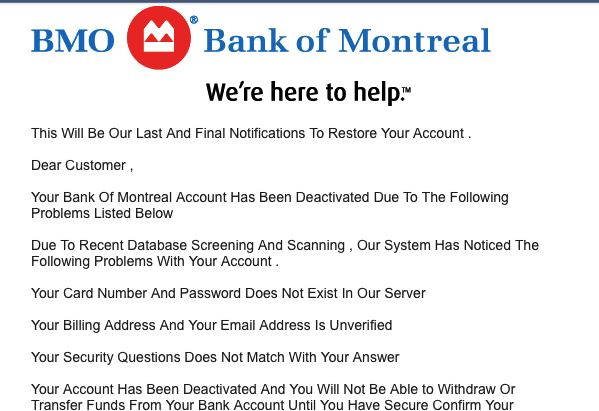
bogus Bank of Montreal email pictured above was a link - it
read:
Confirm and verify my account but
it
pointed to a link reading
pnhs.edu.bd/wp-admin/css-login-bmo/
- not the real Bank of Montreal web address, bmo.com. (But it included
'login-bmo' to try to look legitimate).
Clicking on
this link opens up a PDF version
of an email that my friend Jane sent me - it claimed to be from Apple,
noting an attempt to sign into
iMessage
that might have been bogus. There are several hints that this email is
phony - near the top, it reads:
From:
Apple [mailto:noreply@nibpk.com] - Apple would almost certainly not
send email from an account named '
noreply@nibpk.com'.
That however, could be controlled by a more sophisticated scammer.
Further down, there's a warning in
bright red,
added automatically by Gmail. It tells us that the link claiming to be '
https://appleid.apple.com'
actually points to a very different web address, with a '.
ru'
domain meaning it's somewhere in Russia. Even without that warning,
hovering the mouse over the link (without clicking it!) would show the
actual address where that link points.
(Note that none of the links
exist in this PDF version of the email - hovering your mouse over them
won't show anything!)
Know a little bit about file types and the three-letter extensions at
the ends of file names (often hidden) - many bogus 'naughty neighbour'
email messages include a link promising to get you in touch with
someone in your neighbourhood who's anxious to meet you. Typically,
hovering my mouse over these links shows me something
including
the 3-letter extension 'php'. That's the file extension
for web-based programs -
not a photo, not a video clip, not a traditional link but probably a
program looking to infect my computer. (Remember - "if it's too good to
be true....")
Don't
click!
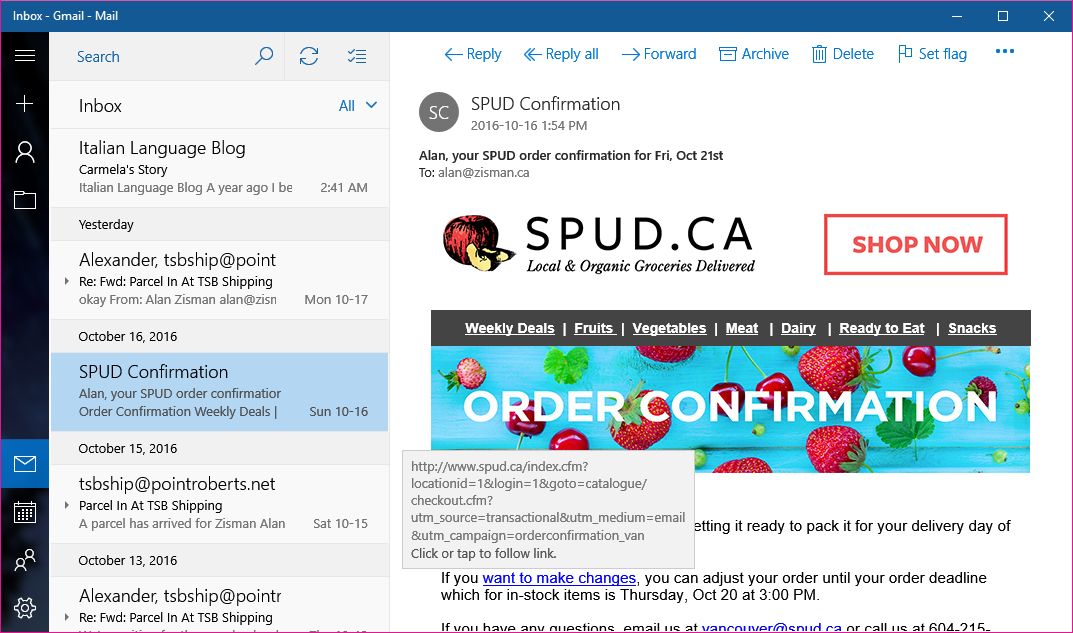
Many email programs do something similar - for instance, in the Windows
10
Mail
app, hovering my mouse
over a link in the legitimate email from local organic food delivery
service SPUD popped up the address of the link - note that it appears
to be legitimately at the company's website: spud.ca - as it should be!
Legitimate web addresses will have the text you expect to see near the
beginning of the link, not somewhere in the middle or at the end.
Make sure that your web browser and email software allow you to see
where a link is
really
pointing - start using this feature and learn to tell whether a link
looks legitimate or not.
Just as links can be bogus, you may receive emails pretending to be
from people you know. Here's one I received that claimed to be from my
friend David (last name whited out).
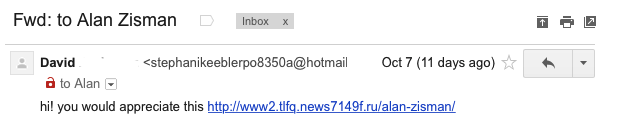
The text is pretty generic -
what's the link pointing to? Why would I
enjoy it? Hovering over the link gives me the same address that appears
in the email's text - but look at the email address beside David's name
- not an address I would expect him to have! Sometimes your email
software may hide the address of people who appear to be in your
contact list, but hovering your mouse will make it appear if you're
suspicious - or clicking on the name. See how you can make the address
appear in the program that you use for email. In the Windows 10 Mail
app, for instance, double-clicking the sender's name opens up a box
that includes the address used to send the message.
How did this happen?
Apparently, some
time in the past David's email address book was hijacked - this might
have involved his computer getting infect but might also have been the
result of a breach at his email service. (For instance, over 500
million Yahoo email users accounts were breached with details becoming
known in 2016 - see: Recognize and secure
a hacked Yahoo Mail account
Note: even
if the email had
shown David's real email address, it still might have been - and in
this case would have been - bogus, wanting me to go to that
suspicious-looking web link.
More: see - Phishing: Would you fall for one
of these scam emails? and
Can
you pass Google's (2019) Phishing Quiz
Second line of defense - your
passwords and PINs
Many of these scam emails are trying to trick you into going to a bogus
website that looks like the log-in page for a bank or online service
where you do business - when you try to log in, they'll have your login
name and password or personal identification number. Then they can use
these to log in as you and potentially empty your bank account or
purchase merchandise and have it be charged to your account or....
If you suspect one or more of your accounts has been breached, the
first thing you should do is log into the real site and change your
password. The sooner you do that, the better.
Passwords, however, can be a problem for a lot of people - many people
are overwhelmed by having too many passwords or use a single password
for everything and/or use a simple, easily guessed password. ('1234',
'abcd', 'qwerty', 'password', etc).
You've probably heard the advice about having complicated passwords
that mix text with numbers (and optionally symbols) and to use a
different passwords for each account - the advice is overwhelming and
the results are almost impossible to remember. Moreover, our computers
offer to remember our passwords - handy, but with the result that if
you have to log in on a different computer or device (or using a
different web browser on the same computer) you may not remember the
password that you used. (Google Chrome and Mozilla Firefox web browsers
let users to create accounts and then save all their passwords online
in their account; logging in to that account on a different computer or
device gives access to all the saved passwords. Similarly, Apple
customers can save passwords to Apple's iCloud - making them available
when they're logged into any Mac, iPhone, or iPad).
There are a several ways to deal with password/PIN overload. Among them:
- Use a password manager
- Here's a 2020 review of 10
password managers. A
password manager stores all your passwords securely on your computer
and automatically enters it as needed when you're browsing the web.
That lets you use a complex password without having to remember/retype
it after the first time. Most password managers can sync between Macs,
PCs, Android and iOS devices. (Often, the free versions of commercial
programs work fine but limit the number of passwords they will store to
5-15 or so - instead, you may want to consider the free Bitwarden. See: Bitwarden vs. LastPass: Which Is the Best Password Manager for You?). More info: https://www.passwordmanager.com/what-is-a-password-manager/
- Use a system to create complex passwords that are memorable
to
you - and only you. Perhaps base them on an old address or phone number
you remember - if you used to live at 879 Oak Street, your Facebook
password could be FB879Oak while your Gmail password could be GM879Oak.
If you need to change one of these passwords (because their server has
been compromised) use your old phone number - change Facebook to
FB8790421.
- Create a spreadsheet for your user accounts, log in names
and
passwords in Microsoft Excel or LibreOffice (or any other software you
use). A spreadsheet provides a grid of rows and columns - perfect for
this sort of information even if you don't have any spreadsheet skills.
When you save it for the first time, you can opt to add a password so
that someone else with access to your computer won't be able to view
your passwords. Or save it online on Google Drive or some other cloud
service.
- Or just write them all down in a notebook - keep it
somewhere
where you can find it when needed! A drawer in your desk at home? Just
don't leave post-it notes with your passwords on your computer monitor
at work! (And if you use a laptop, don't keep your notebook in the same
bag as the laptop - if the laptop gets stolen, so does your notebook!)
Many services (Facebook, Gmail, Microsoft, etc) offer a security option
- often referred to as
two-factor
authentication or
two-step
verification. When you set it up, you're - to provide an
extra
level of security - asked for a cell phone number or email address.
Afterwards, if someone - even you - try to log into your account from a
device that's never been used before with that account a text message
or email is sent out with a code number. Before the new log in can
successfully connect, they need to enter that code number.
This ensures that the log in is really from you, since it's unlikely
that the person using your stolen password also has your cell phone.
It can be a bit of a hassle, though, when the new user is actually you
- using your brand new device, for instance, or logging in on a
friend's computer. Maybe the added security is worth it. More info:
https://www.passwordmanager.com/what-is-two-factor-authentication/
Here is information on adding two-factor authentication for:
See:
How
to set up two-factor authentication
Taking two-step
authentication to the next level.
There can be problems getting codes sent as text messages when needed.
For instance, when I'm travelling, I often get a foreign SIM for my
phone. When I do that, I won't receive text messages sent to my
Canadian phone number. Better may be to use codes generated by an app.
The Facebook mobile app inclused a 'Code Generator' function for this.
Google now has a Google Authenticator app for
Android and
iOS. After installing it on your
phone and
setting up your Google security settings
to validate the app, you'll get codes as needed through Authenticator -
no text messages needed - you can even use the Google Authenticator app
to get codes for Facebook or other non-Google accounts. (One limitation
- if you get a new phone, you'll need to move Authenticator from the
old phone to the new one in order to generate valid codes).
See:
Everything you’ve been told about passwords is a lie
Third line of defense:
Security
Software
In addition to learning to recognize scams in email and on websites and
using good passwords, every Windows users should be running some sort
of security software. Recent versions of Windows comes with free basic
security software - a firewall (to block unauthorized access through
the Internet to your computer) and anti-virus software named either
Windows Defender or Microsoft Security Essentials. When you log into
Windows for the first time, you'll get a notification if these are not
enabled.
The firewall is basic but okay - there's probably no need to get
additional free or commercial firewall software. (These may include
options useful to families wanting to restrict when and when their
children go online). Windows Defender and Microsoft Security
Essentials - built into recent Windows versions - have gotten much
better and may be all you need..
Recognizing that, many PC manufacturers include a trial version to a
more effective commercial security program. (They receive money to do
that from the security vendor). While more effective, note that these
packages are trial versions - they typically work for between one and
three months before they need to be purchased - usually with an annual
fee. And if you don't pay the fee, they will no longer update
themselves - and an out of date security program quickly becomes less
and less useful, even if the computer owner thinks they're being
protected.
Alternatively, one of the free packages recommended in PC Magazines
annual
The
Best
Free Antivirus Protection review
does the trick -
look for the products identified with
[EC]
for 'Editor's Choice'. Each will try to up-sell you to their paid
version and will pop up ads and reminders to help make that point. If
you can live with the nagging, the free version will do the job. Just
be prepared to let your anti-virus/security software update itself on a
regular basis. (In 2016, PC Magazine rated Avast, AVG, and Panda the
best free anti-virus programs. Here's PC Magazine's annual guide to
The Best Antivirus Protection
(non-free). In 2016, their winners were McAfee, Webroot, Bitdefender,
Kaspersky and Symantec/Norton.
On my Windows system, I uninstalled the free Avast because I found
their frequent pop-ups to sell paid services annoying, and reverted to
Windows 10's built-in Windows Defender.
Note however the contrarian:
You
Don't Really Need an Anti-Virus App Anymore
(
'Classic' computer
viruses are rare
these days; according to PC Magazine, "ransomware and
data-stealing Trojans are much more common, as are bots that let the
bot-herder rent out your computer for nefarious purposes."
Modern 'anti-virus'
software tries to protect your computer from a wide range of malware -
not jut computer viruses).
However - even with good, up-to-date security software running in the
background, your computer may still become infected. Maybe you clicked
on an ad on a website or a pop-up message that claimed that your
computer was infected, and in the process download a program that
infected your computer.
If you're not sure , see:
10 Signs Your Computer Is Infected With A
Virus
and
7
Signs You've Got
Malware and
How
to Remove Malware From Your PC
Back up your anti-virus/security program with
MalwareBytes
- again it comes in
free and paid versions. The free version does a great job of cleaning
up an already infected computer. In order to get the latest version,
you may want to get it when you think your computer has been infected -
download it using a different, uninfected computer if possible, copy
the installer onto a USB memory stick and install it onto your infected
computer. Then start it up and let it do it's thing. Maybe run it
several times - restarting your computer after each run - until you get
a report that your is clean.
Note: Some security software is bogus - especially programs that want
you to purchase them after popping up messages claiming your computer
is infected. Are you running any of the programs listed in:
This Security Software Is Insecure! 5 Tools
You Should Get Rid Of (Hint: the 5 programs
listed are: Mac Defender, Security Essentials 2010 (
not Microsoft Security Essentials),
MS Antivirus (
not from
Microsoft)
- aka ANG Antivirus, XP Antivirus, Total Security, PC Defender Plus,
AVASoft Professional Antivirus, Privacy Center - aka Safety Center,
Privacy Components, and WinFixer. These programs, claiming to be
security software, are in fact malware.
Windows 10 users may simply stick with the version of Windows Defender
built into Microsoft's latest operating system. See:
4
Reasons to Use Windows Defender in Windows 10
A
free
online virus scanner is offered by the retailer
Best Buy together with anti-virus company Webroot.
About
downloads and attachments: Downloads
and email attachments can be malicious and infect your computer.
Because of this, many people avoid all downloads and email attachments.
That's safe, but on a par with never going in a car because sometimes
there are car accidents. Better is to learn to recognize unwanted and
potentially malicious email attachments and downloads, while taking
advantage of safe, useful, and enjoyable attachments and downloads.
 - Email attachments
- Email attachments
are files
sent along with an email message (files can also be attached to text or
Facebook messages). These files can be photos, short video clips, music
files - all of which are generally harmless - or program files, which
might be dangerous. The key questions are who is sending these and is
it the sort of thing they usually do? I play in several bands - if I
got music files attached in an email from someone I play music with,
that's probably okay - especially if there was a note in the email
talking about the tunes. (Here's a recording of Duke Ellington playing
'Caravan' - give it a listen; I'd like us to try to play this next
Tuesday when we get together).
If I'm not sure, before opening the attachment I can fire up an email
to the friend - creating a new email message, not replying to the
possibly bogus one - asking if they really sent me an attachment. If
they're puzzled, then I know it's bogus.
Note that email
attachments are generally saved to your Downloads folder...
See:
Don’t
Be Fooled By This New “Helpful” Email Scam
- Downloads
- you can download
photos, videos, books and music files over the Internet, as well as
programs. Many or most are harmless - though in some cases they may be
being distributed in violation of copyright. There are lots of free
programs legally distributed online - I've recommended several and
included links in this page. To use them on your computer, you need to
download the installation file and run it to install the program on
your computer.
In some cases, though, downloaded programs can be malicious and install
malware onto your computer. There are several ways this can happen:
--
as the result of clicking on a pop-up message warning that your
computer is infected - remember, any such message is bogus unless it's
from the anti-virus program that you know you installed. And that
software won't pop up message on a website - the messages will
typically show up in the lower-right corner of your screen whether your
web browser is open or not.
-- searching for software - particularly searching for a free (or
'cracked') version of commercial/paid software and going to an unknown
source for the program. If I'm looking for the
malwarebytes
anti-malware software, downloading it from malwarebytes.com or
malwarebytes.org is where I want to go - google also shows me links to
a variety of other download sites. Maybe they're reliable, but maybe
they're trying to trick me into installing a piece of nastiness
pretending to be the real software. As always online, it helps to know
what's a reliable source. Trying to get software for free that's
usually for sale is especially risky, but even searching for
legitimately free programs can be problematic. Best is to go directly
to the source!
-- searching for TV shows or movies can be risky if you're outside of a
known site (like youtube.com). Again, you
may
get a real video file or you may not. Windows by default hides the
final letters of a file name (the file extension) which identify what
sort of file you're getting - this means that a program file (with a
file extension .exe) can be easily disguised as a video file (with file
extension .avi or .mov or .mp4). If you're not sure about a downloaded
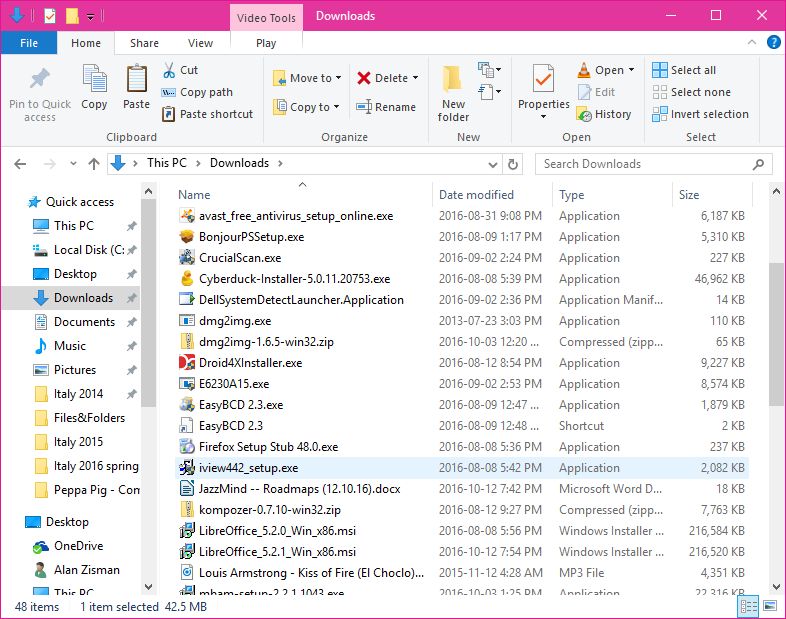
file you could open the Windows File Explorer, switch to Details View,
look at your Downloads folder. The Details view has a Type column - if
the file is identified as a movie, you're good to go.
Notice that in the image on the right, looking in my Downloads folder
there are lots of Applications, a Microsoft Word Document, an MP3
(music) File, and several other file types listed.
See:
Download me—Saying “yes” to the Web’s most
dangerous
search terms
Spam,
phishing, porn and more:
A decade or so ago, people's email inboxes were cluttered with
unwanted and unrequested messages advertising products and soft-core
porn. To a large extent these messages are no longer so visible -
partly the result of legislation but more because of more effective
spam filtering by email providers and built into email software.
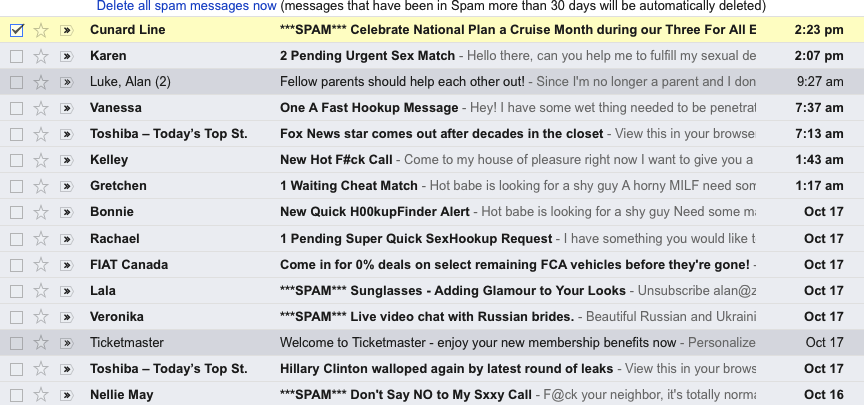
Most of our email accounts include a spam folder - if something that
you think is spam
does land
in your email in-box, you can send it to the spam folder - which may
increase the accuracy of your spam filtering. Your spam filtering makes
the opposite mistake as well, however.... flagging a legitimate message
as spam and automatically putting it in the spam folder without showing
it to you first. If you miss a message that you expect, check the spam
folder. (For instance, while Google/Gmail's spam filtering is very
good, it routinely puts messages from Amazon telling me that a package
I ordered has shipped, in my spam folder).
So it's worth peeking into your spam folder from time to time - if you
see messages there that you want, you should mark them as 'not spam' or
move them to your in-box. On the right is some of the spam folder for
my Gmail account. Note that Google automatically deletes any message
that's over 30 days old in the spam folder.
Notice that some of the messages:
Cunard
Line,
Fiat
Canada for
instance are from legitimate companies who have me on their email list.
If I cared to read them, I might mark them as non-spam. Many of them
appear to be porn - they're not. Instead, like the message claiming to
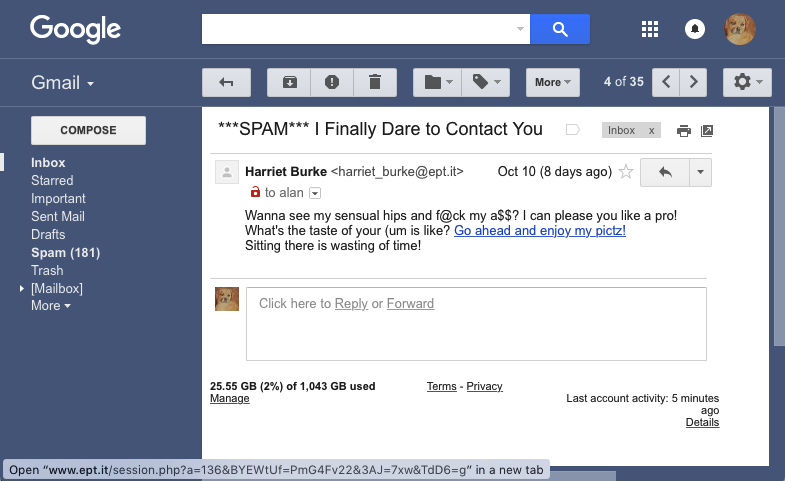
be from 'Harriet Burke' near the beginning of this page, they include
links to 'php' files that would probably install malware on my computer
or try to steal my contact list or hijack my email software. The
message claiming to be from BMO/Bank fo Montreal illustrated above was
also in my spam folder.
Much of
what's in
the spam folder isn't old-style harmless but irritating spam - instead
it's email messages attempting to infect my computer or steal money.
If I open a message that's in my spam folder, Gmail doesn't let me see
any of the questionable links - protecting me from clicking on them by
mistake. If I move those messages back to my in-box, however, I'm no
longer protected from my own stupidity. Still, moving an email from
Amazon about a package that I know I ordered is pretty safe!
More: See:
Don’t
Be Fooled By This New “Helpful” Email Scam
The
phone call from 'Microsoft
Windows': Microsoft does not have employees
checking
server logs to identify computers that are infected, not does it
contract out to other companies to do that. Any phone call that you
receive telling you that your computer is infected is bogus - just as
any message that pops up on your screen saying your computer is
infected is bogus - unless it identifies itself as being from the
anti-virus/security program that you have installed (and pops up as a
standard Windows notification).
The phones were very common a few years ago and seemed to be targetting
seniors in particular. The general process was for the caller to
identify themselves as being from Microsoft (or from Windows or
Microsoft Windows) and saying that they'd noticed from online logs that
your computer was infected. If you didn't hang up immediately, they
would claim that they could verify this - asking you to go to your
computer and search for a particular filename - which would always
appear to be on your computer (assuming it was a Windows computer -
they named a standard Windows file).
Once you were convinced that your computer was infected, they might
walk you through the process of installing
remote
access software - which is often used legitimately by tech support
people to allow them to make changes to a remote computer. Once that
was installed they could do what they wanted at your computer - often
installing bogus anti-virus software. (They may at that point ask for a
credit card number to pay for their 'service'.) Often, the installed
program does nasty things to your system - malware or ransomware and
requires that you pay to have it de-activated or removed.
See:
Microsoft's advice: Hang up on tech
support scammers and
We
talked to Windows tech support scammers. Here's why you shouldn't
and
How
to Discourage Windows Tech Support Scammers When They Call You
In a late-2016 twist on this scam, fake installers for Microsoft's
Security Essentials software claims that your computer is infected and
ask you to phone a number for help to get it cleaned up. See:
Microsoft:
Beware this fake Windows BSOD from tech support scammers' malware
In March 2017 there were reports of a hack of Apple's iCloud service -
emails and phone calls claiming to be from Apple are equally bogus!
Sometimes if your computer
has
been infected with ransomware, you'll
find that your computer's documents have been encrypted - and that only
the people who infected your computer know the secret password needed
to make them usable again.
In that case, the best thing you can do - best of a bad set of choices
- may be to pay up and hope that the ransomware will be removed.
Increasingly, ransomware has been targetting organizations like
hospitals and schools - but individuals are still being targetted as
well.
See:
Why ransomware is booming in 2016
and
Beat
Scammers With These Ransomware Decryption Tools
and
Ransomware
is about to get a lot worse, by holding your operating system hostage
and
Ransomware:
A guide to one of the biggest menaces on the web
and
After
WannaCry, Should You Worry About Ransomware?
Maybe it's not your fault
- If your friends are getting emails claiming to be from you that you
didn't send, it might be that your computer has been compromised. But
it's more and more likely that it's not your fault - instead, an online
service where you have an account may have been compromised. Why spend
time trying to hack your computer when by hacking an online server you
can get account information for tens of millions of accounts. For
instance:
- in October 2013, 153 million Adobe accounts were
breached
- in August 2016, Dropbox
forced millions of users to reset their passwords - later, 68 million
Dropbox user accounts were traded online
- in May 2016, 164 million LinkedIn users'
logins and passwords were compromised
- also in May 2016, 360 RealSpace
logins and passwords were offered for sale
- in January 2017 a RiverCity
Media spam list with 393 million email addresses was
posted online - these were being used to distribute spam.
- in September 2017, US credit bureau Equifax announced
that "identifying information for 143 million customers had potentially been compromised." (!)
When you hear reports that an online service you use was compromised,
go there directly (i.e. type the service's address in your web browser)
and change your password. Don't trust emails claiming to be from the
service asking you to click on a link to change your password - that
could easily be a fraudulent link trying to steal your log-in info.
Instantly check whether your email address has been 'pwned' (i.e.
compromised) at
Have
I Been Pwned
If you've got an Apple iCloud account, see:
How
to protect your Apple iCloud account
Worst-case
scenario: one more reason you need a backup strategy!
Whenever you have a computer problem, tech support people will ask if
you have a backup. Making backups means you have copies of your
documents and programs and can use the backup copy if some sort of
problem - anything from a physical hard drive crash to theft or other
loss to software disaster like ransomware or virus - makes it
impossible to use the original copy.
In a worst-case digital security situation, if you have a backup you -
or tech support people - can restore your computer to its original out
of the box condition, then restore your backup and get your computer
back to the state it was in when you made your backup. You would only
lose files created or changed since you made the backup. (This assumes
that your backup wasn't infected with whatever infected your computer!)
Windows 10, for instance, includes
System Restore and Factory Restore
options as well as a
built-in backup program.
Also see:
If
we show you how to back up your PC for free, will you finally do it?


 Your
bank or online services such as Paypal, Apple iTunes Store,
or others will never email you to tell you your account has been put on
hold or to change your password. They don't do that - if you're unsure
about an email message, go to the company's website - without clicking
a link in the email - and contact them directly. Or phone your bank.
Canada Revenue Agency or the US IRS will never email you to say you get
(or owe) money. Never!
Your
bank or online services such as Paypal, Apple iTunes Store,
or others will never email you to tell you your account has been put on
hold or to change your password. They don't do that - if you're unsure
about an email message, go to the company's website - without clicking
a link in the email - and contact them directly. Or phone your bank.
Canada Revenue Agency or the US IRS will never email you to say you get
(or owe) money. Never! The
first problem is that often online - both on a web page and in an
email message - you can't easily tell where clicking on a link will
take you. Just because something on a webpage or in an email message
says it goes to (say) TD
Bank doesn't mean it really
goes to that bank. Even if the text looks like it's a web address: www.tdbank.com
it could actually point somewhere else - in both cases,
these
links go to my website: http://zisman.ca.
The
first problem is that often online - both on a web page and in an
email message - you can't easily tell where clicking on a link will
take you. Just because something on a webpage or in an email message
says it goes to (say) TD
Bank doesn't mean it really
goes to that bank. Even if the text looks like it's a web address: www.tdbank.com
it could actually point somewhere else - in both cases,
these
links go to my website: http://zisman.ca.
 The text is pretty generic -
what's the link pointing to? Why would I
enjoy it? Hovering over the link gives me the same address that appears
in the email's text - but look at the email address beside David's name
- not an address I would expect him to have! Sometimes your email
software may hide the address of people who appear to be in your
contact list, but hovering your mouse will make it appear if you're
suspicious - or clicking on the name. See how you can make the address
appear in the program that you use for email. In the Windows 10 Mail
app, for instance, double-clicking the sender's name opens up a box
that includes the address used to send the message.
The text is pretty generic -
what's the link pointing to? Why would I
enjoy it? Hovering over the link gives me the same address that appears
in the email's text - but look at the email address beside David's name
- not an address I would expect him to have! Sometimes your email
software may hide the address of people who appear to be in your
contact list, but hovering your mouse will make it appear if you're
suspicious - or clicking on the name. See how you can make the address
appear in the program that you use for email. In the Windows 10 Mail
app, for instance, double-clicking the sender's name opens up a box
that includes the address used to send the message. - Email attachments
are files
sent along with an email message (files can also be attached to text or
Facebook messages). These files can be photos, short video clips, music
files - all of which are generally harmless - or program files, which
might be dangerous. The key questions are who is sending these and is
it the sort of thing they usually do? I play in several bands - if I
got music files attached in an email from someone I play music with,
that's probably okay - especially if there was a note in the email
talking about the tunes. (Here's a recording of Duke Ellington playing
'Caravan' - give it a listen; I'd like us to try to play this next
Tuesday when we get together).
- Email attachments
are files
sent along with an email message (files can also be attached to text or
Facebook messages). These files can be photos, short video clips, music
files - all of which are generally harmless - or program files, which
might be dangerous. The key questions are who is sending these and is
it the sort of thing they usually do? I play in several bands - if I
got music files attached in an email from someone I play music with,
that's probably okay - especially if there was a note in the email
talking about the tunes. (Here's a recording of Duke Ellington playing
'Caravan' - give it a listen; I'd like us to try to play this next
Tuesday when we get together). Most of our email accounts include a spam folder - if something that
you think is spam does land
in your email in-box, you can send it to the spam folder - which may
increase the accuracy of your spam filtering. Your spam filtering makes
the opposite mistake as well, however.... flagging a legitimate message
as spam and automatically putting it in the spam folder without showing
it to you first. If you miss a message that you expect, check the spam
folder. (For instance, while Google/Gmail's spam filtering is very
good, it routinely puts messages from Amazon telling me that a package
I ordered has shipped, in my spam folder).
Most of our email accounts include a spam folder - if something that
you think is spam does land
in your email in-box, you can send it to the spam folder - which may
increase the accuracy of your spam filtering. Your spam filtering makes
the opposite mistake as well, however.... flagging a legitimate message
as spam and automatically putting it in the spam folder without showing
it to you first. If you miss a message that you expect, check the spam
folder. (For instance, while Google/Gmail's spam filtering is very
good, it routinely puts messages from Amazon telling me that a package
I ordered has shipped, in my spam folder).